Data breaches have become an all-consuming topic of late. Stories about data theft dominate political headlines, boardroom discussions and family meetings around the dinner table. They, of course, have also been the subject of government investigations and private litigation.
The current environment is not unlike other moments in the recent past that seem to have captured the attention of Wall Street, K Street and Main Street, including the financial reporting scandals of the early 2000s. During the financial reporting scandals in the early 2000s, regulators and private litigants looked not only to the entities and their executives committing the fraud, but also to the so-called “watchdogs” — financial statement auditors. Plaintiffs alleging securities fraud claimed that the auditor must have known about the fraud, or should have discovered it, regardless of what the fraud was, or whether it touched on a subject within the auditor’s purview.
In response, the accounting profession developed a series of standards that minimized the auditor’s exposure in litigation for things not squarely within the area of an auditor’s responsibility. These standards, promulgated by the American Institute of CPAs, clarify the scope of an auditor’s responsibility, define the responsibilities of the audit client and dictate how the results of the auditor’s work should be communicated. They are intended to “reduce the risk that management may inappropriately rely on the auditor to protect management against certain risks or to perform certain functions that are management's responsibility.” (AU-C § 210, Terms of Engagement, A22).
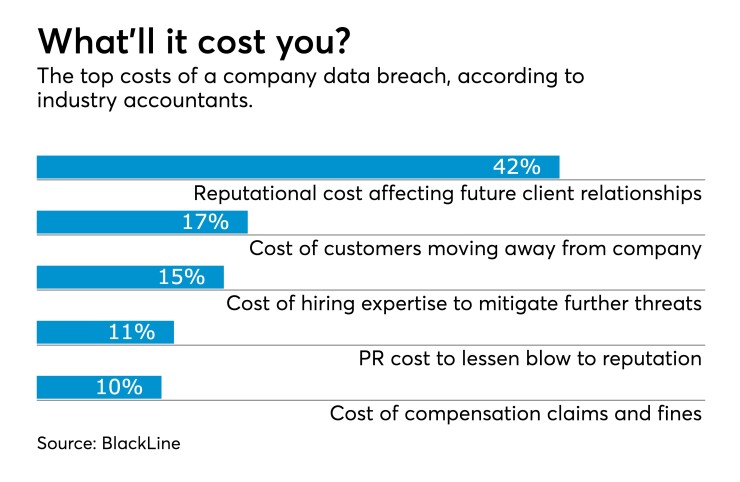
Here are three measures developed by accounting firms that should be adopted by cybersecurity professionals to minimize litigation risk:
1. Define the scope, objectives, and limitations of the work
AICPA standards require that auditors document the terms of an audit engagement in a written engagement letter to confirm “that a common understanding of the terms of the audit engagement exists.” (AU-C § 210) The written engagement agreement must speak to the scope and objective of the audit engagement, and make clear that, “because of the inherent limitations of an audit … an unavoidable risk exists that some material misstatements may not be detected, even though the audit is properly planned and performed in accordance with [generally accepted auditing standards].” (AU-C § 210.10).
The AICPA standards provide a sample engagement letter with language addressing these requirements:
“We will conduct our audit in accordance with auditing standards generally accepted in the United States of America (GAAS). Those standards require that we plan and perform the audit to obtain reasonable assurance about whether the financial statements are free from material misstatement. … Because of the inherent limitations of an audit … an unavoidable risk that some material misstatements may not be detected exists, even though the audit is properly planned and performed in accordance with GAAS.”
Through this language, the auditor identifies:
- The professional standards that will govern the work (GAAS);
- The objective of the work to be performed (to obtain “reasonable assurance” that the financial statements are free of material misstatement); and
- The “unavoidable risk” that even if the audit is correctly planned and performed, a material misstatement may go undetected.
The AICPA also requires financial statement auditors to describe in the engagement letter the expected form and content of the report to be issued at the conclusion of the work.
Likewise, cybersecurity auditors should incorporate these features into their engagement agreements. For instance, where a cybersecurity professional is performing a security risk assessment, the engagement agreement should state which frameworks its process will follow, including those accepted by HIPAA, the Office of Civil Rights, the Payment Card Industry Security Standards Council and the Center for Medicare & Medicaid Services. The agreement should also clarify where there are inherent limitations that would prevent any audit or assessment, even those perfectly planned and executed, from catching all security-related issues. Finally, cybersecurity auditors should preview the expected content of any report to issue after the work is complete.
2. Define the client’s responsibilities
Financial statement auditors are required by professional standards to have their clients confirm in the engagement letter certain of the client’s responsibilities in connection with the audit. (AU-C § 210.10) The audit client’s management must acknowledge that they are responsible for preparing the financial statements, as well as giving the auditor access to all relevant information and persons within the organization from whom the auditor deems it necessary to obtain evidence. (AU-C § 210.06.b)
Cybersecurity auditors should also insist that their engagement agreements detail their client’s responsibilities that are important to the audit or assessment. For instance, the client should agree that it has the responsibility to provide all necessary information concerning any security incident that prompted the need for the cybersecurity professional’s services. The client should also agree to grant access to all systems within the scope of the audit, as well as to all individuals with sufficient authority to schedule testing and deal with other issues as they arise. A cybersecurity auditor may also want the client to agree to maintain a stable configuration over their network until the audit is complete (or as stable as is reasonably feasible). Finally, the cybersecurity auditor should make clear in the engagement agreement that the client’s failure to comply with its obligations may preclude the auditor from completing its work.
3. Precisely communicate the result of the auditor’s work
Even with a perfectly articulated engagement agreement that incorporates the first two elements described above, the work necessary to minimize litigation risk is far from complete. The end product of the auditor’s work must also precisely communicate the auditor’s conclusions and define, again, the scope of the work supporting the conclusions and any inherent limitations. It is not enough to rely on the language of an engagement agreement because a report generated at the conclusion of the work is a separate statement that an unhappy client, or possibly a third party, could claim contains misrepresentations. In that scenario, a cybersecurity auditor will want to point to any limitations and caveats in the final report itself to make clear that the report as a whole is accurate and a fair representation of the work performed and conclusions reached.
For these reasons, AICPA standards require financial statement auditors to identify in their audit report which financial statements covering which periods were audited, explain management’s responsibilities in preparing the financial statement and explain the nature of the auditor’s work and inherent limitations thereof. Cybersecurity professionals should similarly structure their final reports to avoid any potential confusion between the content and scope of its report and the nature and limitations of the work agreed to by the parties at the outset of the arrangement.