The Internal Revenue Service and its tax industry partners warned tax professionals Tuesday that takeovers of tax professionals’ accounts by cybercriminals are on the rise.
The warning is part of a new public awareness campaign by the IRS, state tax authorities and tax industry leaders called “Don’t Take the Bait,” warning tax professionals about email phishing schemes and other tactics used by identity thieves, hackers and fraudsters (see IRS starts education campaign for tax pros on phishing).
The IRS noted that account takeovers occur when a thief manages to steal or guess the username and password of a tax professional. That allows a cybercriminal to access the tax professional’s computers or other online accounts. Thieves can then use the credentials to gain access to a tax professional’s IRS e-Services account to steal their Electronic Filing Identification Number or their tax software account to get their hands on taxpayer information.
“We urge tax professionals to be on the lookout for the warning signs of these schemes and many others that can contribute to data loss and identity theft,” said IRS Commissioner John Koskinen in a statement. “A few simple steps can protect tax professionals as well as their clients.”
The IRS acknowledged that tax professionals and taxpayers aren’t the only group facing the threat of account takeovers.
According to a recent annual report by Javelin Strategy and Research, there was a surge in account takeover incidents nationwide this year, typically aimed at financial accounts, after years of decline. Javelin saw a 31 percent increase in the number of incidents this year.

The emails sent by cybercriminals can look convincing, appearing to originate from IRS E-Services with subject lines such as "Account Closure Now," "Avoid Account Shutdown," or "Unlock Your Account Now," and the IRS included a screen capture of one of them:
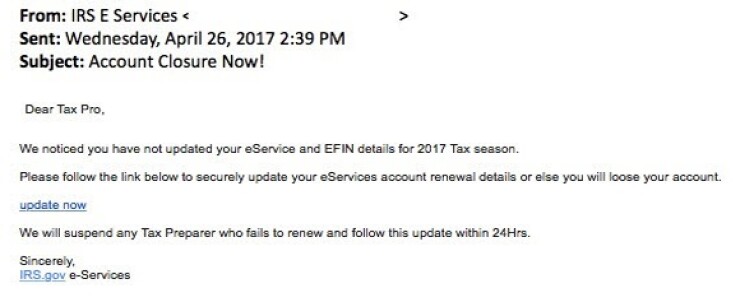
Similarly, thieves can fake the login screen to trick tax professionals into believing it is a genuine IRS site:

The IRS suggested tax pros hover their cursors over a suspicious link in an email to view the destination. It could be a shortened URL such as bit.ly; ow.ly; or tinyurl.com, as opposed to an actual IRS.gov web page. The bogus link would then take the practitioner to a website designed to appear like an authentic e-Services login page.
Separately, on Tuesday, a group of Republican lawmakers questioned the IRS's own email practices, in response to a
House Ways and Means Committee Chairman Kevin Brady, R-Texas, Senate Finance Committee Chairman Orrin Hatch, R-Utah, and House Ways and Means Oversight Subcommittee Chairman Vern Buchanan, R-Fla., asked for a briefing with Koskinen to discuss the IRS’s procedures for retaining and producing electronic documents.
“The lack of an electronic mail system that is compliant with Federal records management requirements and could allow the IRS to retain and search the records of current and separated employees is unacceptable,” the lawmakers wrote in a letter Tuesday. “Failure to retain and produce records reduces transparency, inhibits Congressional oversight, and opens the IRS to judicial sanctions during litigation. TIGTA's findings are also symptomatic of the IRS's shambolic information technology modernization efforts. The production of IRS e-mails as part of external records requests currently relies on the continued integrity and retrievability of thousands of individual employees' hard drives; or, alternatively, relies on IRS employees to print and file important e-mails. Neither system is sustainable, reliable, or scalable to satisfy the voluminous document productions that are required of the IRS."
Buchanan has scheduled a subcommittee hearing on the matter for next Tuesday, July 25.





